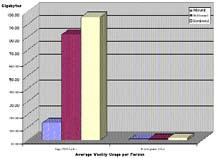
At Cornell University,the top 20 internet users use more bandwifth than the rest of the 5000 student users combined.This chart shows the Average Internet Usage Per ResNet Subscriber at Cornell. (//www.cit.cornell.edu/computer/students/)
Universal Studios has contacted Lawrence within the past month regarding copyrighted material that is being distributed from computers connected to the Lawrence network. According to Universal, some users of Lawrence’s network have been identified as distributing digital copies of Universal movies. They have demanded that the users remove the material or face further legal action.
According to Dean Nancy Truesdell, around a dozen students have been called in to speak with her on an individual basis regarding the letters received by Universal. So far, students have been cooperative in complying with requests to voluntarily remove all copyrighted material from their computers.
As long as the students voluntarily remove the offending files noted by Universal, and they agree not to trade or download any copyrighted material, no further action will be taken.
Truesdell said that this approach would continue as long as no users incurred second violations. If students repeatedly were found to share copyrighted material, further action, such as turning off network accounts, would be taken.
Since distributing copyrighted material is a violation of the computer use policy as outlined in the student handbook, offenders could face judicial repercussions as well.
Many have identified peer-to-peer networks, such as KaZaA, as being major contributors to illegally traded files. Aside from aiding in the easy distribution of copyrighted material, Kazaa also contributes to bandwidth problems for many schools.
According to a Cornell Chronicle article on the subject, “At Cornell, the single largest use of the Internet is for sending outbound KaZaA files. KaZaA is a program used mainly for sharing music and video files. Last year, users sent more than 100,000 gigabytes worth of KaZaA files from Cornell’s network.”
Robert Lowe, network manager at Lawrence, says many schools have implemented a bandwidth quota system that limits bandwidth for those users who use an excessive amount in a short time, often one hour. Lowe also notes that Cornell University has implemented more drastic bandwidth restrictions that measure usage per individual IP and charge users for using over two gigs a month.
Lowe says, “We have no plans, or a budget, to implement any of these approaches.”
He adds, “We prioritize some traffic, but only in an attempt to minimally ensure some fairness. Still, it is not uncommon at Lawrence for five or six registered student computers to use over 30 percent of the available bandwidth.”
When asked whether further measures should be taken by Lawrence to limit the trading of copyrighted material, Lowe asked, “Why should any be taken? Students are capable of making informed decisions. Downloading copyrighted material is clearly breaking the law and not a wise choice, but many do it anyway.”
Peer-to-peer networks concerned with maintaining anonymity for users, such as FreeNet (http://www.freenetproject.org) and FreeHaven (http://www.freehaven.net), have developed after concerns that corporations and government agencies could monitor files shared by users.
According to the FreeNet website, “The main aim of Freenet is to help preserve freedom of speech on the Internet. To achieve this freedom, the network is built first and foremost with anonymity in mind. Without anonymity there can never be true freedom of speech as it is then open to censorship.”
Students interested in securing files stored on their hard drives might consider products such as those produced by PGP (http://www.pgp.com/products/), which offer encryption using algorithms with a minimum 128-bit symmetrical crypto key length. They offer a freeware and a commercial version for a variety of platforms.
According to the National Institute of Standards and Technology, “assuming that one could build a machine that could recover a [128-bit] key in a second, then it would take that machine approximately 149 trillion years to crack a 128-bit AES key. To put that into perspective, the universe is believed to be less than 20 billion years old.
